What are the latest CompTIA CASP CAS-003 exam tips? Get the latest exam questions online practice tests. “CompTIA Advanced Security Practitioner (CASP)” CAS-003 exam. Get the full CompTIA CAS-003 exam dump: https://www.leads4pass.com/cas-003.html (full exam dump)
CompTIA CAS-003 Exam pdf
[PDF Q1-Q13] Free CompTIA CAS-003 pdf dumps download from Google Drive: https://drive.google.com/open?id=1TDaRBZ–ooDf8I_yYC68UPyfsbawfcAj
CompTIA Advanced Security Practitioner (CASP+): https://www.comptia.org/certifications/comptia-advanced-security-practitioner
CASP+ covers the technical knowledge and skills required to conceptualize, engineer, integrate and implement secure solutions across complex environments to support a resilient enterprise.
Latest CompTIA CAS-003 Online Exam Practice Questions
QUESTION 1
The finance department has started to use a new payment system that requires strict PII security restrictions on various
network devices. The company decides to enforce the restrictions and configure all devices appropriately. Which of the
following risk response strategies is being used?
A. Avoid
B. Mitigate
C. Transfer
D. Accept
Correct Answer: D
QUESTION 2
An organization is selecting a SaaS provider to replace its legacy, in house Customer Resource Management (CRM)
application. Which of the following ensures the organization mitigates the risk of managing separate user credentials?
A. Ensure the SaaS provider supports dual factor authentication.
B. Ensure the SaaS provider supports encrypted password transmission and storage.
C. Ensure the SaaS provider supports secure hash file exchange.
D. Ensure the SaaS provider supports role-based access control.
E. Ensure the SaaS provider supports directory services federation.
Correct Answer: E
A SaaS application that has a federation server within the customer\\’s network that interfaces with the customer\\’s own
enterprise user-directory service can provide single sign-on authentication. This federation server has a trust
relationship with a corresponding federation server located within the SaaS provider\\’s network.
Single sign-on will mitigate the risk of managing separate user credentials.
QUESTION 3
Within the past six months, a company has experienced a series of attacks directed at various collaboration tools.
Additionally, sensitive information was compromised during a recent security breach of a remote access session from
an unsecure site. As a result, the company is requiring all collaboration tools to comply with the following:
Secure messaging between internal users using digital signatures Secure sites for video-conferencing sessions
Presence information for all office employees Restriction of certain types of messages to be allowed into the network.
Which of the following applications must be configured to meet the new requirements? (Select TWO.)
A. Remote desktop
B. VoIP
C. Remote assistance
D. Email
E. Instant messaging
F. Social media websites
Correct Answer: BE
QUESTION 4
An architect was recently hired by a power utility to increase the security posture of the company\\’s power generation
and distribution sites. Upon review, the architect identifies legacy hardware with highly vulnerable and unsupported
software driving critical operations. These systems must exchange data with each other, be highly synchronized, and
pull from the Internet time sources. Which of the following architectural decisions would BEST reduce the likelihood of a
successful attack without harming operational capability? (Choose two.)
A. Isolate the systems on their own network
B. Install a firewall and IDS between systems and the LAN
C. Employ own stratum-0 and stratum-1 NTP servers
D. Upgrade the software on critical systems
E. Configure the systems to use government-hosted NTP servers
Correct Answer: BE
QUESTION 5
A Chief Financial Officer (CFO) has raised concerns with the Chief Information Security Officer (CISO) because money
has been spent on IT security infrastructure, but corporate assets are still found to be vulnerable. The business recently
funded a patch management product and SOE hardening initiative. A third party auditor reported findings against the
business because some systems were missing patches. Which of the following statements BEST describes this
situation?
A. The CFO is at fault because they are responsible for patching the systems and have already been given patch
management and SOE hardening products.
B. The audit findings are invalid because remedial steps have already been applied to patch servers and the
remediation takes time to complete.
C. The CISO has not selected the correct controls and the audit findings should be assigned to them instead of the
CFO.
D. Security controls are generally never 100% effective and gaps should be explained to stakeholders and managed
accordingly.
Correct Answer: D
Security controls can never be run 100% effective and is mainly observed as a risk mitigation strategy thus the gaps
should be explained to all stakeholders and managed accordingly.
QUESTION 6
A risk manager has decided to use likelihood and consequence to determine the risk of an event occurring to a
company asset. Which of the following is a limitation of this approach to risk management?
A. Subjective and based on an individual\\’s experience.
B. Requires a high degree of upfront work to gather environment details.
C. Difficult to differentiate between high, medium, and low risks.
D. Allows for cost and benefit analysis.
E. Calculations can be extremely complex to manage.
Correct Answer: A
Using likelihood and consequence to determine risk is known as qualitative risk analysis.
With qualitative risk analysis, the risk would be evaluated for its probability and impact using a numbered ranking
system such as low, medium, and high or perhaps using a 1 to 10 scoring system.
After qualitative analysis has been performed, you can then perform quantitative risk analysis. A Quantitative risk
analysis is a further analysis of the highest priority risks during which a numerical or quantitative rating is assigned to the
risk.
Qualitative risk analysis is usually quick to perform and no special tools or software is required. However, qualitative risk
analysis is subjective and based on the user\\’s experience.
QUESTION 7
Given the code snippet below: Which of the following vulnerability types in the MOST concerning?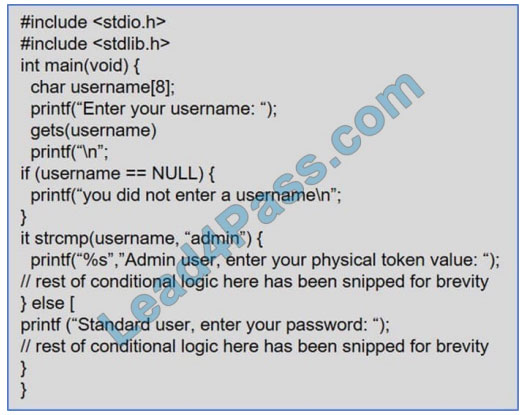
A. Only short usernames are supported, which could result in brute forcing of credentials.
B. Buffer overflow in the username parameter could lead to a memory corruption vulnerability.
C. Hardcoded usernames with different code paths taken depend on which user is entered.
D. Format string vulnerability is present for admin users but not for standard users.
Correct Answer: B
QUESTION 8
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has
determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can
view the outbound callback traffic, but sees no traffic between the two computers. Which of the following would BEST
address the IDS visibility gap?
A. Install network taps at the edge of the network.
B. Send syslog from the IDS into the SIEM.
C. Install HIDS on each computer.
D. SPAN traffic form the network core into the IDS.
Correct Answer: D
QUESTION 9
Customers are receiving emails containing a link to malicious software. These emails are subverting spam filters. The
email reads as follows:
Delivered-To: [email protected]
Received: by 10.14.120.205
Mon, 1 Nov 2010 11:15:24 -0700 (PDT)
Received: by 10.231.31.193
Mon, 01 Nov 2010 11:15:23 -0700 (PDT)
Return-Path:
Received: from 127.0.0.1 for ; Mon, 1 Nov 2010 13:15:14 -0500 (envelope-from )
Received: by smtpex.example.com (SMTP READY)
with ESMTP (AIO); Mon, 01 Nov 2010 13:15:14 -0500 Received: from 172.18.45.122 by 192.168.2.55; Mon, 1 Nov
2010 13:15:14 -0500 From: Company To: “[email protected]” Date: Mon, 1 Nov 2010 13:15:11 -0500 Subject:
New Insurance Application Thread-Topic: New Insurance Application Please download and install software from the site
below to maintain full access to your account. www.examplesite.com
Additional information: The authorized mail servers IPs are 192.168.2.10 and 192.168.2.11.
The network\\’s subnet is 192.168.2.0/25.
Which of the following are the MOST appropriate courses of action a security administrator could take to eliminate this
risk? (Select TWO).
A. Identify the origination point for malicious activity on the unauthorized mail server.
B. Block port 25 on the firewall for all unauthorized mail servers.
C. Disable open relay functionality.
D. Shut down the SMTP service on the unauthorized mail server.
E. Enable STARTTLS on the spam filter.
Correct Answer: BD
In this question, we have an unauthorized mail server using the IP: 192.168.2.55.
Blocking port 25 on the firewall for all unauthorized mail servers is a common and recommended security step. Port 25
should be open on the firewall to the IP addresses of the authorized email servers only (192.168.2.10 and
192.168.2.11).
This will prevent unauthorized email servers sending email or receiving and relaying email.
Email servers use SMTP (Simple Mail Transfer Protocol) to send email to other email servers. Shutting down the SMTP
service on the unauthorized mail server is effectively disabling the mail server functionality of the unauthorized server.
QUESTION 10
During a new desktop refresh, all hosts are hardened at the OS level before deployment to comply with policy. Six
months later, the company is audited for compliance to regulations. The audit discovers that 40 percent of the desktops
do not meet requirements. Which of the following is the MOST likely cause of the noncompliance?
A. The devices are being modified and settings are being overridden in production.
B. The patch management system is causing the devices to be noncompliant after issuing the latest patches.
C. The desktop applications were configured with the default username and password.
D. 40 percent of the devices use full disk encryption.
Correct Answer: A
The question states that all hosts are hardened at the OS level before deployment. So we know the desktops are fully
patched when the users receive them. Six months later, the desktops do not meet the compliance standards. The most
likely for this is that the users have changed the settings of the desktops during the six months that they\\’ve had them.
QUESTION 11
The network administrator at an enterprise reported a large data leak. One compromised server was used to aggregate
data from several critical application servers and send it out to the Internet using HTTPS. Upon investigation, there have
been no user logins over the previous week and the endpoint protection software is not reporting any issues. Which of
the following BEST provides insight into where the compromised server collected the information?
A. Review the flow data against each server\\’s baseline communications profile.
B. Configure the server logs to collect unusual activity including failed logins and restarted services.
C. Correlate data loss prevention logs for anomalous communications from the server.
D. Setup a packet capture on the firewall to collect all of the server communications.
Correct Answer: A
Network logging tools such as Syslog, DNS, NetFlow, behavior analytics, IP reputation, honeypots, and DLP solutions
provide visibility into the entire infrastructure. This visibility is important because signature-based systems are no longer
sufficient for identifying the advanced attacker that relies heavily on custom malware and zero-day exploits. Having
knowledge of each host\\’s communications, protocols, and traffic volumes as well as the content of the data in question
is key to identifying zero-day and APT (advance persistent threat) malware and agents. Data intelligence allows forensic
analysis to identify anomalous or suspicious communications by comparing suspected traffic patterns against normal
data communication behavioral baselines. Automated network intelligence and next-generation live forensics provide
insight into network events and rely on analytical decisions based on known vs. unknown behavior taking place within a
corporate network.
QUESTION 12
A Chief Information Security Officer (CISO is reviewing and revising system configuration and hardening guides that
were developed internally and have been used several years to secure the organization\\’s systems.
The CISO knows improvements can be made to the guides.
Which of the following would be the BEST source of reference during the revision process?
A. CVE database
B. Internal security assessment reports
C. Industry-accepted standards
D. External vulnerability scan reports
E. Vendor-specific implementation guides
Correct Answer: A
QUESTION 13
As part of an organization\\’s compliance program, administrators must complete a hardening checklist and note any
potential improvements. The process of noting improvements in the checklist is MOST likely driven by:
A. the collection of data as part of the continuous monitoring program.
B. adherence to policies associated with incident response.
C. the organization\\’s software development life cycle.
D. changes in operating systems or industry trends.
Correct Answer: A
Share leads4pass discount codes for free

About leads4pass!
leads4pass offers the latest exam exercise questions for free! CompTIA exam questions are updated throughout the year. leads4pass has many professional exam experts! Guaranteed valid passing of the exam! The highest pass rate, the highest cost-effective! Help you pass the exam easily on your first attempt.
Summarize:
AllaboutExams shares the latest CompTIA CASP CAS-003 exam dumps, CAS-003 pdf, CAS-003 exam exercise questions for free. You can improve your skills and exam experience online to get complete exam questions and answers guaranteed to pass the exam we recommend leads4pass CAS-003 exam dumps
Latest update leads4pass CAS-003 exam dumps: https://www.leads4pass.com/cas-003.html (530 Q&As)
[Q1-Q13 PDF] Free CompTIA CAS-003 pdf dumps download from Google Drive: https://drive.google.com/open?id=1TDaRBZ–ooDf8I_yYC68UPyfsbawfcAj