
EC-COUNCIL 312-50V11 Dumps includes dumps pdf and dumps vce: https://www.leads4pass.com/312-50v11.html (PDF+VCE). leads4pass has a complete EC-COUNCIL 312-50V11 Dumps to help you successfully pass the exam.
All exam content on this website is provided by leads4pass. leads4pass updates all exam questions and answers throughout the year. We will share the latest dumps for each update. Today we share the latest updated EC-COUNCIL 312-50V11 free dumps. You can take the exam online. The answers to the exam are announced at the end of the article.
And we will also share all collections of EC-COUNCIL 312-50V11 exam PDF
Google Drive:
[Free-1] https://drive.google.com/file/d/1qpSn4H2LdsN-NioFOR0Ln59YfJ2_FQGY/view?usp=sharing
[Free-2] https://drive.google.com/file/d/17-fQhaMT4pabFAeEFEFB3sEKYFQaMBnf/view?usp=sharing
[Free-3] https://drive.google.com/file/d/1ap2P_piJ8AP8BkaxrqHnXqc1XjVbrYaN/view?usp=sharing
[Free-4] https://drive.google.com/file/d/10VAQob2giQ-xeTwFx-xjMXI9wBiCctuA/view?usp=sharing
EC-COUNCIL 312-50V11 Free Dumps
Question 1:
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.
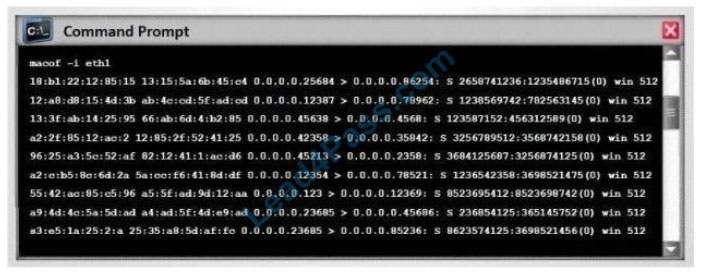
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
A. Switch then acts as hub by broadcasting packets to all machines on the network
B. The CAM overflow table will cause the switch to crash causing Denial of Service
C. The switch replaces outgoing frame switch factory default MAC address of FF:FF:FF:FF:FF:FF
D. Every packet is dropped and the switch sends out SNMP alerts to the IDS port
Question 2:
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist\’s email, and you send her an email changing the source email to her boss\’s email (boss@company). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don\’t work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network. What testing method did you use?
A. Social engineering
B. Piggybacking
C. Tailgating
D. Eavesdropping
Question 3:
Study the following log extract and identify the attack.
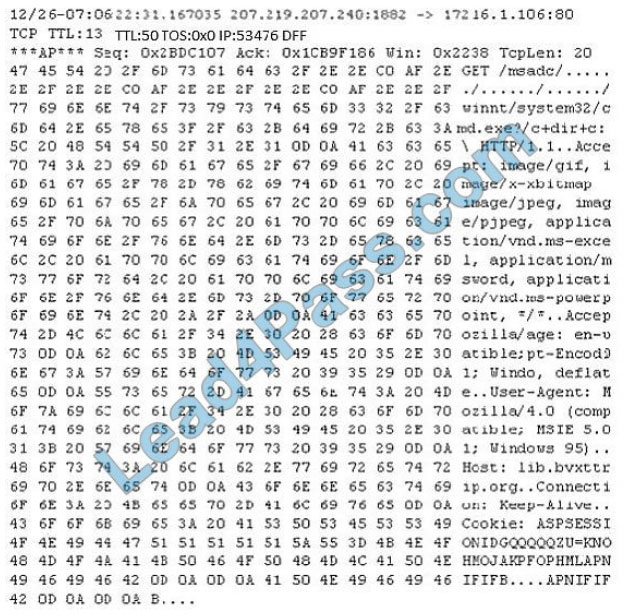
A. Hexcode Attack
B. Cross Site Scripting
C. Multiple Domain Traversal Attack
D. Unicode Directory Traversal Attack
Question 4:
One of your team members has asked you to analyze the following SOA record.
What is the TTL? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
A. 200303028
B. 3600
C. 604800
D. 2400
E. 60
F. 4800
Question 5:
Techno Security Inc. recently hired John as a penetration tester. He was tasked with identifying open ports in the target network and determining whether the ports are online and any firewall rule sets are encountered. John decided to perform a TCP SYN ping scan on the target network. Which of the following Nmap commands must John use to perform the TCP SVN ping scan?
A. nmap -sn -pp < target ip address >
B. nmap -sn -PO < target IP address >
C. Anmap -sn -PS < target IP address >
D. nmap -sn -PA < target IP address >
Question 6:
In the context of password security, a simple dictionary attack involves loading a dictionary file (a text file full of dictionary words) into a cracking application such as L0phtCrack or John the Ripper, and running it against user accounts located by the application. The larger the word and word fragment selection, the more effective the dictionary attack is. The brute force method is the most inclusive, although slow. It usually tries every possible letter and number combination in its automated exploration. If you would use both brute force and dictionary methods combined together to have variation of words, what would you call such an attack?
A. Full Blown
B. Thorough
C. Hybrid
D. BruteDics
Question 7:
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in bounds checking mechanism?
Code:
#include int main(){char buffer[8];
strcpy(buffer, “”11111111111111111111111111111″”);} Output: Segmentation fault
A. C#
B. Python
C. Java
D. C++
Question 8:
Heather\’s company has decided to use a new customer relationship management tool. After performing the appropriate research, they decided to purchase a subscription to a cloud-hosted solution. The only administrative task that Heather will need to perform is the management of user accounts. The provider will take care of the hardware, operating system, and software administration including patching and monitoring. Which of the following is this type of solution?
A. SaaS
B. IaaS
C. CaaS
D. PasS
Software as a service (SaaS) allows users to attach to and use cloud-based apps over the web. Common examples ar email, calendaring and workplace tool (such as Microsoft workplace 365). SaaS provides a whole software solution that you get on a pay-as-you-go basis from a cloud service provider. You rent the use of an app for your organisation and your users connect with it over the web, typically with an internet browser. All of the underlying infrastructure, middleware, app software system and app knowledge ar located within the service provider\’s knowledge center. The service provider manages the hardware and software system and with the appropriate service agreement, can make sure the availability and also the security of the app and your data as well. SaaS allows your organisation to induce quickly up and running with an app at token upfront cost. Common SaaS scenariosThis tool having used a web-based email service like Outlook, Hotmail or Yahoo! Mail, then you have got already used a form of SaaS. With these services, you log into your account over the web, typically from an internet browser. the e- mail software system is found on the service provider\’s network and your messages ar hold on there moreover. you can access your email and hold on messages from an internet browser on any laptop or Internet-connected device. The previous examples are free services for personal use. For organisational use, you can rent productivity apps, like email, collaboration and calendaring; and sophisticated business applications like client relationship management (CRM), enterprise resource coming up with (ERP) and document management. You buy the use of those apps by subscription or per the level of use. Advantages of SaaSGain access to stylish applications. to supply SaaS apps to users, you don\’t ought to purchase, install, update or maintain any hardware, middleware or software system. SaaS makes even sophisticated enterprise applications, like ERP and CRM, affordable for organisations that lack the resources to shop for, deploy and manage the specified infrastructure and software system themselves. Pay just for what you utilize. you furthermore may economize because the SaaS service automatically scales up and down per the level of usage. Use free shopper software system. Users will run most SaaS apps directly from their web browser without needing to transfer and install any software system, though some apps need plugins. this suggests that you simply don\’t ought to purchase and install special software system for your users. Mobilise your hands simply. SaaS makes it simple to “mobilise” your hands as a result of users will access SaaS apps and knowledge from any Internet-connected laptop or mobile device. You don\’t ought to worry concerning developing apps to run on differing types of computers and devices as a result of the service supplier has already done therefore. additionally, you don\’t ought to bring special experience aboard to manage the safety problems inherent in mobile computing. A fastidiously chosen service supplier can make sure the security of your knowledge, no matter the sort of device intense it. Access app knowledge from anyplace. With knowledge hold on within the cloud, users will access their info from any Internet-connected laptop or mobile device. And once app knowledge is hold on within the cloud, no knowledge is lost if a user\’s laptop or device fails.
Question 9:
This TCP flag instructs the sending system to transmit all buffered data immediately.
A. SYN
B. RST
C. PSH
D. URG
E. FIN
Question 10:
What hacking attack is challenge/response authentication used to prevent?
A. Replay attacks
B. Scanning attacks
C. Session hijacking attacks
D. Password cracking attacks
Question 11:
Which of the following is the best countermeasure to encrypting ransomwares?
A. Use multiple antivirus softwares
B. Pay a ransom
C. Keep some generation of off-line backup
D. Analyze the ransomware to get decryption key of encrypted data
Question 12:
Eve is spending her day scanning the library computers. She notices that Alice is using a computer whose port 445 is active and listening. Eve uses the ENUM tool to enumerate Alice machine. From the command prompt, she types the following command.
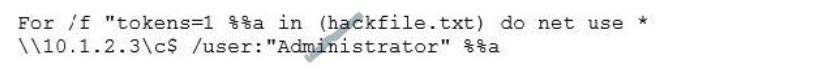
What is Eve trying to do?
A. Eve is trying to connect as a user with Administrator privileges
B. Eve is trying to enumerate all users with Administrative privileges
C. Eve is trying to carry out a password crack for user Administrator
D. Eve is trying to escalate privilege of the null user to that of Administrator
Question 13:
A post-breach forensic investigation revealed that a known vulnerability in Apache Struts was to blame for the Equifax data breach that affected 143 million customers. A fix was available from the software vendor for several months prior 10 the Intrusion. This Is likely a failure in which of the following security processes?
A. vendor risk management
B. Security awareness training
C. Secure deployment lifecycle
D. Patch management
Question 14:
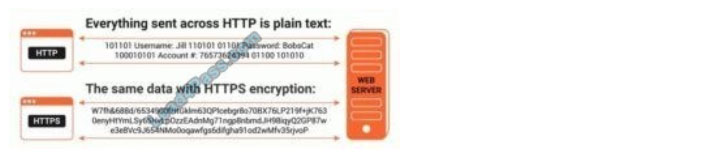
Bella, a security professional working at an it firm, finds that a security breach has occurred while transferring important files. Sensitive data, employee usernames. and passwords are shared In plaintext, paving the way for hackers 10 perform successful session hijacking. To address this situation. Bella Implemented a protocol that sends data using encryption and digital certificates. Which of the following protocols Is used by Bella?
A. FTP
B. HTTPS
C. FTPS
D. IP
HTTPS is the shortening for hypertext move convention secure, or secure hypertext move convention in the event that you are not a fanatic for semantics. How Does HTTPS Work?Dissimilar to HTTP, HTTPS utilizes a protected testament from an outsider seller to make sure about an association and confirm that the site is genuine. This safe authentication is known as a SSL Certificate (or “cert”). SSL is a truncation for “secure attachments layer”. This is the thing that makes a safe, encoded association between a program and a worker, which secures the layer of correspondence between the two. This declaration encodes an association with a degree of insurance that is assigned at your season of the acquisition of a SSL endorsement. A SSL endorsement gives an additional layer of security for touchy information that you don\’t need outsider aggressors to get to. This extra security can be critical with regards to running online business sites. A few Examples: When you need to make sure about the transmission of Mastercard information or other delicate data, (for example, somebody\’s genuine location and actual personality). When you run a lead age site that depends on somebody\’s genuine data, wherein case you need to utilize HTTPS to protect against malevolent assaults on the client\’s information. There are numerous advantages to HTTPS that merit the slight expense. Keep in mind, if the declaration is absent, an outsider could undoubtedly check the association for delicate information.
What is TLS? How it Applies to HTTPSTLS represents transport layer security. It encodes HTTPS and can be utilized to make sure about email and different conventions. It utilizes cryptographic methods that guarantee information has not been altered since it was sent, that interchanges are with the real individual the correspondence came from, and to keep private information from being seen. Things kick off with a TLS handshake, the cycle that commences a correspondence meeting that utilizes TLS encryption. This is the place where verification happens, and meeting keys are made. Shiny new meeting keys are produced when two gadgets impart, from the two unique keys cooperating. The consequence of this is more profound, more encoded correspondence. A Critical Step for HTTPS — Authenticating the Web ServerThe most basic advance for a HTTPS secure association is guaranteeing that a web worker is who they say they are. That is the reason the SSL authentication is the main piece of this arrangement; it guarantees the proprietor of the webserver is who they say the declaration says it is. It working correspondingly to how a driver\’s permit functions — it affirms the character of the proprietor of the worker. A layer of assurance from specific kinds of assaults exists when you actualize HTTPS, making this an important staple of your site.
Question 15:
Which of the following tools can be used for passive OS fingerprinting?
A. nmap
B. tcpdump
C. tracert
D. ping
Announce the answer:
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| A | A | D | D | C | C | D | A | C | A | C | C | D | B | B |
Complete EC-COUNCIL 312-50V11 dumps: https://www.leads4pass.com/312-50V11.html (Total Questions: 250 Q&A)
Download the EC-COUNCIL 312-50V11 exam PDF collection for free
Google Drive:
[Free-1] https://drive.google.com/file/d/1qpSn4H2LdsN-NioFOR0Ln59YfJ2_FQGY/view?usp=sharing
[Free-2] https://drive.google.com/file/d/17-fQhaMT4pabFAeEFEFB3sEKYFQaMBnf/view?usp=sharing
[Free-3] https://drive.google.com/file/d/1ap2P_piJ8AP8BkaxrqHnXqc1XjVbrYaN/view?usp=sharing
[Free-4] https://drive.google.com/file/d/10VAQob2giQ-xeTwFx-xjMXI9wBiCctuA/view?usp=sharing
This site collects the latest updated EC-COUNCIL 312-50V11 Free Dumps for you, and the EC-COUNCIL 312-50V11 exam PDFs from different periods. Everything is to help you take the exam.
Finally, I wish you good luck always! Like, please bookmark and share! thanks.
PS. EC-COUNCIL includes many series: CEH v10, CEH v11, ECSA, etc., all free exam questions and answers can be obtained in latestvce.com